Discover how to secure your website effortlessly with our guide to Install Lets Encrypt Certificate on Linux. Follow simple steps to enhance your website’s security and build trust with visitors. Implementing SSL/TLS encryption has never been easier – safeguard your online presence today.”
Introduction:
In today’s digital age, keeping your website secure is more crucial than ever. One powerful way to enhance your website’s security is by installing an SSL/TLS certificate. In this blog, we’ll walk you through the process of installing a Let’s Encrypt certificate on your Linux server, ensuring your visitors’ data is encrypted and your website is trustworthy.
Understanding Lets Encrypt:
Lets Encrypt is like the superhero of SSL certificates—it’s free, automated, and widely trusted. Its mission is to make the internet a safer place by providing everyone with easy access to secure connections.
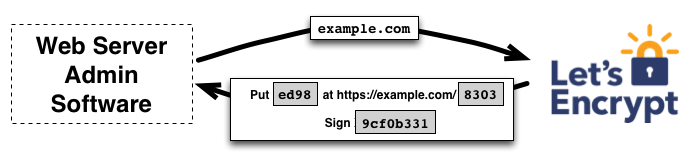
How Lets Encrypt Works:
Lets Encrypt uses a fancy protocol called ACME (Automated Certificate Management Environment) to automatically validate and issue certificates. This means less hassle for you, and your certificates get renewed automatically.
Read Also How to Configure Nginx? The Top 10 Useful Nginx Configurations
How to Install Lets Encrypt Certificate on Linux
Prerequisites:
Before we dive into the installation, make sure you have:
- A Linux server (Ubuntu, Debian, CentOS, etc.).
- Administrative (sudo) access to your server.
- Apache or Nginx web server installed.
HTTP Challange (Default Method)
HTTP challenge is the default and preferred method. If the Server is public then it is very easy to set up following the below steps. However, for wild card Domain or DNS Preferred Method please see the DNS Challenge Method further below #generate-lets-encrypt-certificate-with-dns-challenge
Install Certbot:
First things first, let’s get Certbot, the tool that makes installing Lets Encrypt certificates a breeze.
sudo apt-get update sudo apt-get install certbotCertbot Commands:
Certbot comes with simple commands to manage your certificates. For example, to get a certificate, you just need to run
sudo certbot certonly --webroot -w /var/www/html -d yourdomain.com Replace "yourdomain.com" with your actual domain.Requesting a Certificate: Certbot will prompt you for some information and, voilà, you’ll have your certificate. It’s like magic, but for website security!
Configuring Your Web Server:
For Apache:
If you’re using Apache, Certbot will automatically configure it for you. All you need to do is reload Apache.
sudo service apache2 reloadFor Nginx:
For Nginx users, Certbot does the heavy lifting, and a quick Nginx reload is all you need.
sudo service nginx reloadTesting and Troubleshooting:
Now that you’re all set up, it’s a good idea to test your SSL configuration. Open your browser, go to your website using “https://” and make sure everything looks secure.
If you run into any issues, don’t worry! Certbot has a helpful community, and you can often find solutions with a quick online search.
Automating Certificate Renewal:
Certificates need a bit of love every now and then. Luckily, Certbot handles this too! Set up a cron job to automatically renew your certificate.
sudo crontab -eAdd the following line to renew every week (for the Nginx example, please change it to the desired web service):
0 0 * * 0 sudo /usr/bin/certbot renew --post-hook "systemctl reload nginx"To change the time and schedule. Please modify the cron referring to this article
Generate Lets Encrypt Certificate with DNS Challenge
There may be a requirement when you need to create an SSL Certificate for the Websites working on Local IPs. This can be achieved but the only prerequisite is you need to at least Public DNS so that Certbot can verify the Domain Ownership. It will be done by setting the preferred verification mode to DNS challenge
Install the Certbot
sudo apt-get update sudo apt-get install certbotDNS Preferred Challenge Command (Automatic)
The command to generate the certificate using Snap package manger is rather straightforward. You may do it for a single domain; for additional domains, simply append -d DOMAIN.
To Auto Generate Certificate with DNS Provider. There are multiple plugins enabled for DNS providers like Cloudflare, Route53, etc. Please check the complete list here
You need to have the Snap package manager installed, you can install it on any Linux distribution using package managers like apt (for Debian/Ubuntu-based systems) or dnf (for Fedora-based/CentOS systems).
Install Certbot Packages And DNS Plugin
For Debian/Ubuntu-based systems:
sudo apt update
sudo apt install snapdFor Fedora/Centos-based systems:
sudo dnf install snapd
sudo systemctl enable --now snapd.socketCreate a Symlink
For Debian/Ubuntu-based systems:
sudo ln -s /snap/bin/certbot /usr/bin/certbotfor Fedora/CentOS:
ln -s /var/lib/snapd/snap /snapInstall Certbot using snapd
sudo snap install --classic certbotOnce you install the certbot, run the below command
sudo snap set certbot trust-plugin-with-root=okInstall the Cloudflare DNS plugin
for Fedora/CentOS:
sudo yum install python3-certbot-dns-cloudflareFor Debian/Ubuntu-based systems:
sudo apt-get install python3-certbot-dns-cloudflareCreate A Cloudflare API Key Or Token
You need to create an API key that has ‘Zone:DNS:Edit‘ access to the zone of your domain. API Tokens use the standard Authorization.
Please refer to this article for more details about cloudflare api token credentials setup.
Once you get the API key save the key to the Linux machine, following the below steps:
Create the hidden folder and file for security purposes
mkdir -p .certbot/cloudflare
touch .certbot/cloudflare/cloudflare.iniFor the security purpose restrict the file access to 600
chmod 600 .certbot/cloudflare/cloudflare.iniadd your API within the cloudflare.ini file
nano .certbot/cloudflare/cloudflare.inipaste the below config with your api key
# Cloudflare API token used by Certbot
dns_cloudflare_api_token = add_here_your_cloudflare_APINow let’s generate the certificate. Execute the below command
certbot certonly \
--dns-cloudflare \
--dns-cloudflare-credentials ~/.certbot/cloudflare/cloudflare.ini \
--dns-cloudflare-propagation-seconds 60 \
-d example.com \
-d example2.comIf there is no error then Lets encrypt certificate and private key are generated at locations
/etc/letsencrypt/live/<domain>/fullchain.pem
/etc/letsencrypt/live/<domain>/privkey.pem.
You may add the location of the certificates in your web server locations
then it means that the SSL certificate has been configured as well as the Certbot Cloudflare plugin will automatically renew certificates once the certificate expires.
You can verify whether the Certbot renewal process is running in the background or not by using the command provided below
systemctl list-timersThat’s it you have set the Lets Encrypt Auto Renew certificate using DNS preference
DNS Preferred Challenge Command (Manual)
If there is no DNS Provider plugin available or you don’t won’t to delegate the DNS provider access to the Server then please follow the below steps to create the Certificate but it can’t be Automatic and has to be renewed on near expiry. It requires a TXT record to be updated manually as well.
sudo certbot certonly --manual --preferred-challenges dns -d "*.DOMAIN"- Enter the email address
- Press (A) and (Y) for further steps to Agree on some conditions
Once Completed Certbot will attempt to check the DNS but as it fails so it will provide the DNS TXT record to be created in a Domain
Setting DNS TXT ACME Challenge in DNS Provider
It will show the output like below
Please deploy a DNS TXT record under the name:
_acme-challenge.domain.com.
with the following value:
dtfg4T6qHrtdyYd9dtd-4sos2serCsaBsd3j5sddbudf
Please create the TXT record in your Public DNS Provider
Once created, please come back and Press Enter to Continue to verify
It should be successfully completed and you should see the certificate has been issued
Conclusion:
Congratulations! You’ve successfully installed a Lets Encrypt certificate on your Linux server. Your website is now more secure, and your visitors can browse with confidence. Remember, website security doesn’t have to be complicated, and with Lets Encrypt, it’s practically a walk in the park. Happy securing!
Additional Resources:
- Why should you automate Active Directory cleanup? - 17 June 2025
- Troubleshooting: Unable to Add Instance Failover Group to Azure SQL Managed Instance - 4 March 2025
- 10 Azure Virtual Desktop (AVD) Cost-Optimization Strategies for 2025 💡💰 - 22 February 2025



